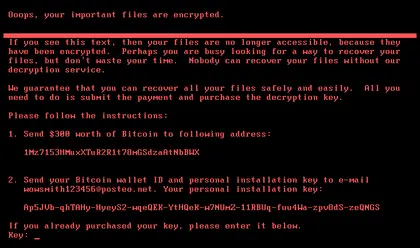
The war with Russia might have already reached the West.
A report prepared by the Henry Jackson Society, a UK-based think tank, on cybersecurity for the UK Parliament has highlighted past and ongoing Russian cyberattacks against targets in Ukraine and the West, including critical infrastructure, with real-world consequences reaching far beyond cyberspace.
JOIN US ON TELEGRAM
Follow our coverage of the war on the @Kyivpost_official.
David Kirichenko, the report’s author, described the Russo-Ukrainian war as the “first all-out cyber war between two nation-states” where Moscow has continued to incorporate cyberattacks with physical strikes, and he emphasized the importance for the West to assist Ukraine and learn from the experience to prepare for future Russian incursions.
“The West must reframe its thinking about how it supports Ukraine and helps to improve Ukraine’s capabilities to conduct a larger cyber offensive against Russia in support of its battlefield objectives.
“Russia’s cyber war against Ukraine and the West is part of its wider campaign to prevail on the physical front and destroy Ukraine before moving further West. Keeping Ukraine alive in the fight and supporting its defense won’t bring victory and peace, but giving Ukraine the abilities and means to win on the digital and physical fronts will protect the Western world,” reads the report.
Collateral Financial Damage to the West
In the report, Kirichenko said cyberattacks against Ukraine could – and had in the past – spill over to the West with real-world consequences, citing the infamous NotPetya attack that took place on Ukraine’s Constitution Day in 2017.
ISW Russian Offensive Campaign Assessment, October, 22, 2024
Tariq Ahmad, UK Minister for Cybersecurity at the Foreign Office, said the attack also cost European organizations hundreds of millions of pounds.
Embedded through backdoor access to a popular accounting software in Ukraine, NotPetya was disguised as ransomware when in reality, its goal was to wipe out data regardless of ransom payment. The UK government claimed Moscow – particularly its military – was behind the attack.
It dealt extensive damage to Ukraine in what former US Department of Homeland Security advisor Tom Bossert described as “using a nuclear bomb to achieve a small tactical victory.”
“The primary objective of NotPetya was to disrupt Ukraine’s financial system, but its effects extended well beyond that as it targeted a wide range of entities including banks, energy companies, government offices, airports and even some non-governmental organizations.
“Within a span of 24 hours, NotPetya managed to erase data from 10 percent of computers across Ukraine, causing widespread disruption across various sectors,” the report reads.
Past Cyberattacks Against Western Targets
In the report, Kirichenko also named multiple Russian cyberattacks in the past – likely supported or sanctioned by the Kremlin – against targets in Europe and the US.
In 2015, Russian hackers breached the computer network of the Bundestag, the German parliament, in what Berlin suspected to be Moscow’s attempt to steal information that could disrupt its elections; a year later, Russian hackers attempted to hack the Christian Democratic Union (CDU), the political party then led by Chancellor Angela Merkel, but to no avail.
The UK has also been a target for Russian hackers, according to the report.
“This included spear phishing attacks on parliamentarians in a range of political parties from 2015 onwards, hacks of UK–US trade documents before the 2019 general election, and breaches of think tanks and civil society organizations,” it reads.
As for the US, the cyberattacks could be directed toward Washington’s national interest, such as in the 2016 elections.
“The most notorious incident occurred in 2016 when there was interference in the US presidential election with Russian hackers breaching the Democratic National Committee and leaking sensitive information to WikiLeaks,” it reads.
Elections aside, there have also been successful attempts to infiltrate US government networks.
“A sophisticated espionage campaign was discovered in 2020 with the SolarWinds hack, which allowed Russian hackers access to numerous companies and US Government agencies through compromised IT management software.
“The SolarWinds cyberattack remained unnoticed for several months while the company distributed software updates embedded with the hackers’ code to its clients globally. This attack enabled hackers to gain access to various US Government networks, including those operated by the Department of Homeland Security and the Treasury Department,” the report reads.
Real-World Ramifications
The cyberattacks on the West also extended to critical infrastructure, including power grids.
“In 2018, the US energy grid and other critical infrastructure sectors faced targeted attacks from Russian Government hackers, prompting a joint government alert between the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI).
“[...] Russia’s goal from the hack was to showcase its growing cyber power and demonstrate its ability to hack critical infrastructure in the US,” reads the report.
Another cyberattack in 2021 – though it might not be sanctioned by the Kremlin – led to severe fuel supply disruption across the US.
“In May 2021, Colonial Pipeline was hit with a ransomware attack by a Russian criminal group that impacted the pipeline’s IT systems. The attack was so devasting it led to jet fuel shortages for airlines and created long queues at petrol stations and a spike in petrol prices.
“People were rushing to fill plastic bags with petrol, and the government had to issue a warning for people to only use containers intended for use with fuel, and several US states had to declare a state of emergency,” the report says.
Food supply chains are not immune to cyberattacks either.
“A month later, JBS Foods, a major meat processing company, fell victim to a ransomware attack by a Russia-based group, forcing all nine of its beef plants to temporarily close. The attack also affected its poultry and pork processing plants in the US.
“This shutdown had serious implications for the meat supply chain in the US, with concerns about potential shortages and spikes in meat prices,” it adds.
Ongoing Attacks
Kirichenko also noted the decentralization of cyberattacks in his report, where non-state actors have a growing role in carrying out cyber offensives against state actors.
However, Kirichenko also noted Moscow’s failure to “successfully integrate cyber and conventional attacks on the battlefield” due to “the apparent lack of synchronization between Russia’s cyber operations and its ground forces.”
Nonetheless, cyberattacks on the West have continued.
“Another prominent group in this cyber offensive is NoName057(16), known for its manifesto that criticizes the West for ‘Russophobia.’ [...] Since its inception in early 2022, NoName057(16) has rapidly expanded its reach, garnering over 52,000 subscribers by September 2023.
“The group’s cyberattacks have had a wide impact, disrupting the financial sector in Denmark, port operations in Dutch cities like Amsterdam and Groningen, and a range of businesses in Poland and Lithuania. Similar attacks were conducted against the Icelandic parliament and the Council of Ministers, whose websites [were] brought down by DDoS attacks from NoName057,” the report reads.
Kirichenko added that while there are likely no direct links between the group and the Kremlin, it is likely “influenced by the desires of the government,” a trend that could be applied to both hacker groups in Ukraine and Russia.
Kirichenko warned that critical infrastructure in the West will likely be targets of Russian hacker groups as the war in Ukraine ground into a stalemate.
“In May 2022, following the arrest of one of its associates, the cyber hacktivist group Killnet issued a threat that it would target critical medical equipment in the UK, specifically lifesaving ventilators in British hospitals.
“A cyberattack that interferes with these systems could lead to delayed or incorrect dispensing of essential drugs, posing serious risks to patient health. The potential impact of such cyberattacks extends beyond individual patient outcomes,” he said.
Kirichenko said “everything and everyone can be a target for hacking” moving forward, and citizens and governments should both be prepared for Russia violating the “basic rules of cyber war,” as it has done so in Ukraine.
The report also covered the cyberwar between Ukraine and Russia in detail and offers advice for private enterprises and governments on mitigating cyber risks based on Ukraine’s experience from the war.
You can read the full report here.
You can also highlight the text and press Ctrl + Enter